Microsoft cannot keep its own security in order, so what hope for its add-ons customers?
Microsoft cannot keep its own security in order, so what hope for its add-ons customers? Go to Source Secure-by-default... if your pockets are deep enough Microsoft has come under fire for charging for security add-ons despite the...
‘ArcaneDoor’ Cyberspies Hacked Cisco Firewalls to Access Government Networks
Sources suspect China is behind the targeted exploitation of two zero-day vulnerabilities in Cisco’s security appliances.
North Korean Hackers Hijack Antivirus Updates for Malware Delivery
A North Korea-linked threat actor hijacked the update mechanism of eScan antivirus to deploy backdoors and cryptocurrency miners. The post North Korean Hackers Hijack Antivirus Updates for Malware Delivery appeared first on SecurityWeek.
Researchers Detail Multistage Attack Hijacking Systems with SSLoad, Cobalt Strike
Cybersecurity researchers have discovered an ongoing attack campaign that's leveraging phishing emails to deliver malware called SSLoad. The campaign, codenamed FROZEN#SHADOW by Securonix, also involves the deployment of Cobalt Strike and the ConnectWise ScreenConnect...
Windows 11 now comes with its own adware
Windows 11 now comes with its own adware Go to Source It used to be that you could pay for a retail version of Windows 11 and expect it to be ad-free, but those days are apparently finito. The latest update to Windows 11 (KB5036980)...
CISA Warns of Windows Print Spooler Flaw After Microsoft Sees Russian Exploitation
CISA Warns of Windows Print Spooler Flaw After Microsoft Sees Russian Exploitation Go to Source CISA warns organizations of a two-year-old Windows Print Spooler vulnerability being exploited in the wild. The post CISA Warns of Windows...
eScan Antivirus Update Mechanism Exploited to Spread Backdoors and Miners
A new malware campaign has been exploiting the updating mechanism of the eScan antivirus software to distribute backdoors and cryptocurrency miners like XMRig through a long-standing threat codenamed GuptiMiner targeting large corporate networks. Cybersecurity firm...
CoralRaider Malware Campaign Exploits CDN Cache to Spread Info-Stealers
A new ongoing malware campaign has been observed distributing three different stealers, such as CryptBot, LummaC2, and Rhadamanthys hosted on Content Delivery Network (CDN) cache domains since at least February 2024. Cisco Talos has attributed the activity with...
Russian Cyberspies Deliver ‘GooseEgg’ Malware to Government Organizations
Russia-linked APT28 deploys the GooseEgg post-exploitation tool against numerous US and European organizations. The post Russian Cyberspies Deliver ‘GooseEgg’ Malware to Government Organizations appeared first on SecurityWeek.
Server Inventory Checklist (Free Download)
Threats from malware, cryptographic infections and compromised networks have never been greater. Headlines regularly attest to such widespread problems, from infection-felled organizations to dangerous vulnerabilities in popular tools. Companies can’t protect their...
Microsoft DRM Hack Could Allow Movie Downloads From Popular Streaming Services
Microsoft DRM Hack Could Allow Movie Downloads From Popular Streaming Services Go to Source Microsoft PlayReady vulnerabilities that could allow rogue subscribers to illegally download movies from popular streaming services. The post...
Adobe claims its new image generation model is its best yet
Firefly, Adobe’s family of generative AI models, doesn’t have the best reputation among creatives. The Firefly image generation model in particular has been derided as underwhelming and flawed compared to Midjourney, OpenAI’s DALL-E 3, and other rivals, with a...
Russia’s APT28 Exploited Windows Print Spooler Flaw to Deploy ‘GooseEgg’ Malware
The Russia-linked nation-state threat actor tracked as APT28 weaponized a security flaw in the Microsoft Windows Print Spooler component to deliver a previously unknown custom malware called GooseEgg. The post-compromise tool, which is said to have been used since at...
Old Windows print spooler bug is latest target of Russia’s Fancy Bear gang
Putin's pals use 'GooseEgg' malware to launch attacks you can defeat with patches or deletion Russian spies are exploiting a years-old Windows print spooler vulnerability and using a custom tool called GooseEgg to elevate privileges and steal credentials across...
If all kernel bugs are security bugs, how do you keep your Linux safe?
Since February, there've been 800 newly assigned CVEs. Your job? Update your main Linux distro more often.

Cyber Security Today, April 22, 2024 -Vulnerability in CrushFTP file transfer software, security updates for Cisco’s controller management application, and more
Vulnerability found in CrushFTP file transfer software, security updates for Cisco’s controller management application, and more. Welcome to Cyber Security Today. It’s Monday April 22nd, 2024. I’m Howard Solomon. A warning is going out about a vulnerability in another...
Copilot auto-launch bug now takes flight in multiple Windows Insider channels
Copilot auto-launch bug now takes flight in multiple Windows Insider channels Go to Source Clippy 2024 is something else Microsoft has acknowledged an error – Copilot is auto-launching for Windows Insiders in the Beta Channel as well...
Researchers Uncover Windows Flaws Granting Hackers Rootkit-Like Powers
Researchers Uncover Windows Flaws Granting Hackers Rootkit-Like Powers Go to Source New research has found that the DOS-to-NT path conversion process could be exploited by threat actors to achieve rootkit-like capabilities to conceal...
T2 – 85,894 breached accounts
In April 2024, 86k records from the T2 tea store were posted to a popular hacking forum. Data included email and physical addresses, names, phone numbers, dates of birth, purchases and passwords stored as scrypt hashes.
Researchers claim Windows Defender can be fooled into deleting databases
Researchers claim Windows Defender can be fooled into deleting databases Go to Source Two rounds of reports and patches may not have completely closed this hole BLACK HAT ASIA Researchers at US/Israeli infosec outfit SafeBreach last...
Ask HN: Please recommend how to manage personal serverss
Hey guys,I'm not an infrastructure engineer nor do I work in web, but I'm pretty comfortable with Linux. I realised I need to spin up a couple of home servers and VPSs to simplify and localise my digital life, and I have an RPi and an x86 NAS in my home network, and a...
GitHub comments abused to push malware via Microsoft repo URLs
GitHub comments abused to push malware via Microsoft repo URLs Go to Source Article URL: https://www.bleepingcomputer.com/news/security/github-comments-abused-to-push-malware-via-microsoft-repo-urls/ Comments URL:...
OpenMetadata Vulnerabilities Exploited to Abuse Kubernetes Clusters for Cryptomining
OpenMetadata Vulnerabilities Exploited to Abuse Kubernetes Clusters for Cryptomining Go to Source Microsoft warns that several OpenMetadata vulnerabilities are being exploited to deploy cryptomining malware to Kubernetes...
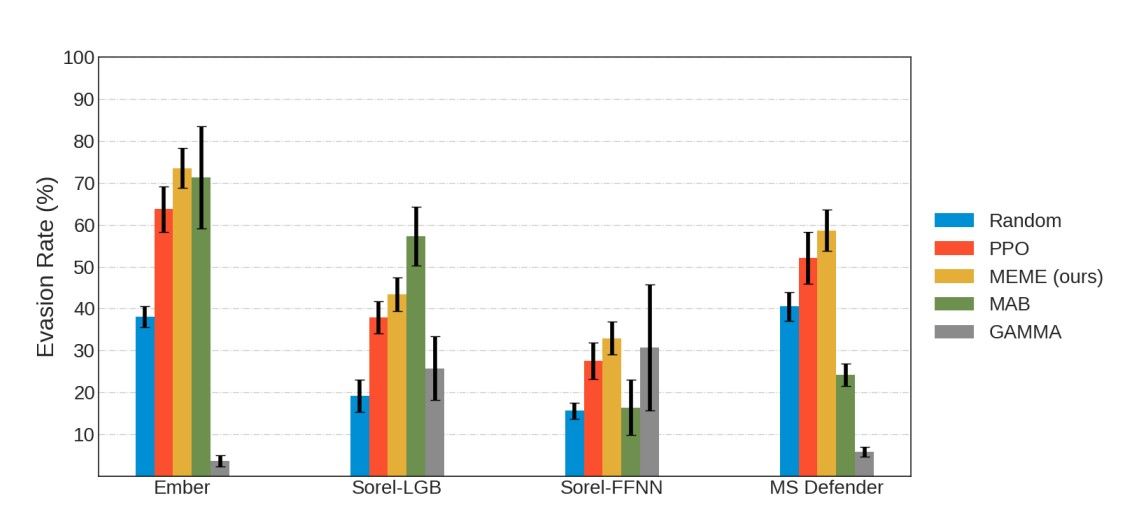
MEME vs. PPO: Analyzing Evasion Rates and Binary Modifications in Malware Detection
:::info Authors: (1) Maria Rigaki, Faculty of Electrical Engineering, Czech Technical University in Prague, Czech Republic and [email protected]; (2) Sebastian Garcia, Faculty of Electrical Engineering, Czech Technical University in Prague, Czech Republic and...
MEME Algorithm’s Impact on Adversarial Malware Generation and Model Evasion
:::info Authors: (1) Maria Rigaki, Faculty of Electrical Engineering, Czech Technical University in Prague, Czech Republic and [email protected]; (2) Sebastian Garcia, Faculty of Electrical Engineering, Czech Technical University in Prague, Czech Republic and...
Crooks exploit OpenMetadata holes to mine crypto – and leave a sob story for victims
Crooks exploit OpenMetadata holes to mine crypto – and leave a sob story for victims Go to Source 'I want to buy a car. That's all' Crooks are exploiting month-old OpenMetadata vulnerabilities in Kubernetes environments to mine...
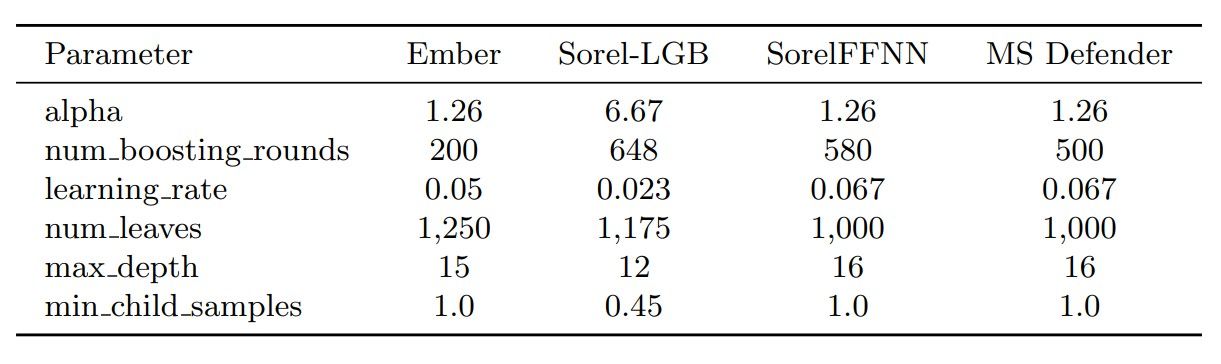
Adversarial Malware Creation with Model-Based Reinforcement Learning: Appendix
:::info Authors: (1) Maria Rigaki, Faculty of Electrical Engineering, Czech Technical University in Prague, Czech Republic and [email protected]; (2) Sebastian Garcia, Faculty of Electrical Engineering, Czech Technical University in Prague, Czech Republic and...
Enhancing Cybersecurity with MEME: Reinforcement Learning for Adversarial Malware Evasion
:::info Authors: (1) Maria Rigaki, Faculty of Electrical Engineering, Czech Technical University in Prague, Czech Republic and [email protected]; (2) Sebastian Garcia, Faculty of Electrical Engineering, Czech Technical University in Prague, Czech Republic and...
Kaspersky Study: Devices Infected With Data-Stealing Malware Increased by 7 Times Since 2020
Nearly 10 million devices were infected with data-stealing malware in 2023, with criminals stealing an average of 50.9 credentials per device.
OfflRouter Malware Evades Detection in Ukraine for Almost a Decade
Select Ukrainian government networks have remained infected with a malware called OfflRouter since 2015. Cisco Talos said its findings are based on an analysis of over 100 confidential documents that were infected with the VBA macro virus and uploaded to the...
