Understanding Microsoft’s Trusted Signing service
Understanding Microsoft’s Trusted Signing service Go to Source How do we ensure that the code we’re installing is, at the very least, the code that a vendor shipped? The generally accepted solution is code signing, adding a digital...
New Cuttlefish Malware Hijacks Router Connections, Sniffs for Cloud Credentials
A new malware called Cuttlefish is targeting small office and home office (SOHO) routers with the goal of stealthily monitoring all traffic through the devices and gather authentication data from HTTP GET and POST requests. "This malware is modular, designed primarily...
Adobe Adds Content Credentials and Firefly to Bug Bounty Program
Adobe is providing incentives for bug bounty hackers to report security flaws in its implementation of Content Credentials and Adobe Firefly. The post Adobe Adds Content Credentials and Firefly to Bug Bounty Program appeared first on SecurityWeek.
Cuttlefish Malware Targets Routers, Harvests Cloud Authentication Data
Cuttlefish malware platform roaming around enterprise SOHO routers capable of covertly harvesting public cloud authentication data from internet traffic. The post Cuttlefish Malware Targets Routers, Harvests Cloud Authentication Data appeared first on SecurityWeek.
Android Malware Wpeeper Uses Compromised WordPress Sites to Hide C2 Servers
Cybersecurity researchers have discovered a previously undocumented malware targeting Android devices that uses compromised WordPress sites as relays for its actual command-and-control (C2) servers for detection evasion. The malware, codenamed Wpeeper, is an ELF...
Adobe Adds Firefly and AI Watermarking to Bug Bounty Program
Researchers can earn up to $10,000 for critical vulnerabilities in the generative AI products.
Adobe wants your help finding security flaws in Content Credentials and Firefly
Adobe is expanding its bug bounty program. If you're an ethical hacker or a security researcher, here's how you can join (and earn rewards).
ZLoader Malware Evolves with Anti-Analysis Trick from Zeus Banking Trojan
The authors behind the resurfaced ZLoader malware have added a feature that was originally present in the Zeus banking trojan that it's based on, indicating that it's being actively developed. "The latest version, 2.4.1.0, introduces a feature to prevent execution on...
Docker Hub Users Targeted With Imageless, Malicious Repositories
JFrog raises an alarm after finding three large-scale malware campaigns targeting Docker Hub with imageless repositories. The post Docker Hub Users Targeted With Imageless, Malicious Repositories appeared first on SecurityWeek.
Google search for “Delta Emulator” shows malware as top result
Article URL: https://www.google.com/search?q=delta+emulator Comments URL: https://news.ycombinator.com/item?id=40211604 Points: 11 # Comments: 5
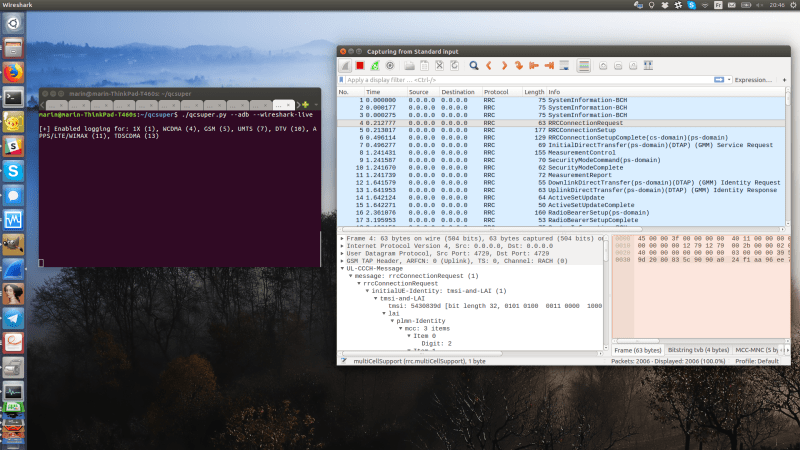
Turn Your Qualcomm Phone Or Modem Into Cellular Sniffer
If your thought repurposing DVB-T dongles for generic software defined radio (SDR) use was cool, wait until you see QCSuper, a project that re-purposes phones and modems to capture raw 2G/3G/4G/5G. You have to have a Qualcomm-based device, it has to either run rooted...
You Can Use Visual Studio Code To Write Commodore 64 Assembly
You Can Use Visual Studio Code To Write Commodore 64 Assembly Go to Source Once upon a time, you might have developed for the Commodore 64 using the very machine itself. You’d use the chunky old keyboard, a tape drive, or the 1541...
MovieBoxPro – 6,009,014 breached accounts
In April 2024, over 6M records from the streaming service MovieBoxPro were scraped from a vulnerable API. Of questionable legality, the service provided no contact information to disclose the incident, although reportedly the vulnerability was rectified after being...
Google Prevented 2.28 Million Malicious Apps from Reaching Play Store in 2023
Google on Monday revealed that almost 200,000 app submissions to its Play Store for Android were either rejected or remediated to address issues with access to sensitive data such as location or SMS messages over the past year. The tech giant also said it blocked...
Honeywell: USB Malware Attacks on Industrial Orgs Becoming More Sophisticated
An analysis conducted by Honeywell shows that much of the USB-borne malware targeting industrial organizations can still cause OT disruption. The post Honeywell: USB Malware Attacks on Industrial Orgs Becoming More Sophisticated appeared first on SecurityWeek.
Ukraine Targeted in Cyberattack Exploiting 7-Year-Old Microsoft Office Flaw
Ukraine Targeted in Cyberattack Exploiting 7-Year-Old Microsoft Office Flaw Go to Source Cybersecurity researchers have discovered a targeted operation against Ukraine that has been found leveraging a nearly seven-year-old flaw in...
Bogus npm Packages Used to Trick Software Developers into Installing Malware
An ongoing social engineering campaign is targeting software developers with bogus npm packages under the guise of a job interview to trick them into downloading a Python backdoor. Cybersecurity firm Securonix is tracking the activity under the...
BeyondTrust Report: Microsoft Security Vulnerabilities Decreased by 5% in 2023
BeyondTrust Report: Microsoft Security Vulnerabilities Decreased by 5% in 2023 Go to Source Refreshed software and collaboration with the security researcher community may have contributed to the 5% drop.

This Week in Security: Cisco, Mitel, and AI False Flags
There’s a trend recently, of big-name security appliances getting used in state-sponsored attacks. It looks like Cisco is the latest victim, based on a report by their own Talos Intelligence. This particular attack has a couple of components, and abuses a couple of...
Self-Spreading PlugX USB Drive Malware Plagues Over 90k IP Addresses
More than 90,000 unique IPs are still infected with a PlugX worm variant that spreads via infected flash drives. The post Self-Spreading PlugX USB Drive Malware Plagues Over 90k IP Addresses appeared first on SecurityWeek.

Cyber Security Today, April 26, 2024 – Patch warnings for Cisco ASA gateways and a WordPress plugin
Patch warnings for Cisco ASA gateways and a WordPress plugin. Welcome to Cyber Security Today. It’s Friday, April 26th, 2024. I’m Howard Solomon. Network administrators with Cisco Systems’ ASA security appliance on their networks are urged to install the latest...
New ‘Brokewell’ Android Malware Spread Through Fake Browser Updates
Fake browser updates are being used to push a previously undocumented Android malware called Brokewell. "Brokewell is a typical modern banking malware equipped with both data-stealing and remote-control capabilities built into the malware," Dutch security firm...
Piping Rock – 2,103,100 breached accounts
In April 2024, 2.1M email addresses from the online health products store Piping Rock were publicly posted to a popular hacking forum. The data also included names, phone numbers and physical addresses. The account posting the data had previously posted multiple other...
State-Sponsored Hackers Exploit Two Cisco Zero-Day Vulnerabilities for Espionage
A new malware campaign leveraged two zero-day flaws in Cisco networking gear to deliver custom malware and facilitate covert data collection on target environments. Cisco Talos, which dubbed the activity ArcaneDoor, attributing it as the handiwork of a previously...
Governments issue alerts after ‘sophisticated’ state-backed actor found exploiting flaws in Cisco security boxes
Don't get too comfortable: 'Line Dancer' malware may be targeting other vendors, too A previously unknown and "sophisticated" nation-state group compromised Cisco firewalls as early as November 2023 for espionage purposes — and possibly attacked network devices made...
Cisco Raises Alarm for ‘ArcaneDoor’ Zero-Days Hitting ASA Firewall Platforms
Cisco warns that nation state-backed hackers are exploiting at least two zero-day vulnerabilities in its ASA firewall platforms to plant malware on telecommunications and energy sector networks. The post Cisco Raises Alarm for ‘ArcaneDoor’ Zero-Days Hitting ASA...
Microsoft cannot keep its own security in order, so what hope for its add-ons customers?
Microsoft cannot keep its own security in order, so what hope for its add-ons customers? Go to Source Secure-by-default... if your pockets are deep enough Microsoft has come under fire for charging for security add-ons despite the...
‘ArcaneDoor’ Cyberspies Hacked Cisco Firewalls to Access Government Networks
Sources suspect China is behind the targeted exploitation of two zero-day vulnerabilities in Cisco’s security appliances.
North Korean Hackers Hijack Antivirus Updates for Malware Delivery
A North Korea-linked threat actor hijacked the update mechanism of eScan antivirus to deploy backdoors and cryptocurrency miners. The post North Korean Hackers Hijack Antivirus Updates for Malware Delivery appeared first on SecurityWeek.
Researchers Detail Multistage Attack Hijacking Systems with SSLoad, Cobalt Strike
Cybersecurity researchers have discovered an ongoing attack campaign that's leveraging phishing emails to deliver malware called SSLoad. The campaign, codenamed FROZEN#SHADOW by Securonix, also involves the deployment of Cobalt Strike and the ConnectWise ScreenConnect...
