Beware: Fake Browser Updates Deliver BitRAT and Lumma Stealer Malware
Fake web browser updates are being used to deliver remote access trojans (RATs) and information stealer malware such as BitRAT and Lumma Stealer (aka LummaC2). "Fake browser updates have been responsible for numerous malware infections, including those of the...
Microsoft and ARM: A Rocky Romance A Decade in the Making
Microsoft and ARM: A Rocky Romance A Decade in the Making Go to Source “Microsoft announces new Surface devices! Their light form factor blends the experience of a traditional laptop with a tablet. A new Windows version, specially...

Law enforcement task force shuts down six malware droppers
An international law enforcement task force has disrupted the infrastructure behind six malware droppers, malicious programs that play a key role in hacking campaigns. Europol, which led the task force, announced the development today. The effort included hundreds of...
International Malware Takedown Seized 100+ Servers
‘Operation Endgame’ is an ongoing effort to disrupt botnets, malware droppers and malware-as-a-service.
Mystery miscreant remotely bricked 600,000 SOHO routers with malicious firmware update
Source and motive of 'Pumpkin Eclipse' assault unknown Unknown miscreants broke into more than 600,000 routers belonging to a single ISP late last year and deployed malware on the devices before totally disabling them, according to security researchers.…

This Week in Security: Operation Endgame, Appliance Carnage, and Router Genocide
This week saw an impressive pair of takedowns pulled off by law enforcement agencies around the world. The first was the 911 S5 botnet, Which the FBI is calling “likely the world’s largest botnet ever”. Spreading via fake free VPN services, 911 was actually a massive...
Mysterious Threat Actor Used Chalubo Malware to Brick 600,000 Routers
Over 600,000 SOHO routers belonging to a single ISP and infected with the Chalubo trojan were rendered inoperable. The post Mysterious Threat Actor Used Chalubo Malware to Brick 600,000 Routers appeared first on SecurityWeek.
CISA Warns of Exploited Linux Kernel Vulnerability
CISA instructs federal agencies to mitigate CVE-2024-1086, a Linux kernel flaw leading to privilege escalation. The post CISA Warns of Exploited Linux Kernel Vulnerability appeared first on SecurityWeek.
Russian Hackers Target Europe with HeadLace Malware and Credential Harvesting
The Russian GRU-backed threat actor APT28 has been attributed as behind a series of campaigns targeting networks across Europe with the HeadLace malware and credential-harvesting web pages. APT28, also known by the names BlueDelta, Fancy Bear, Forest Blizzard,...
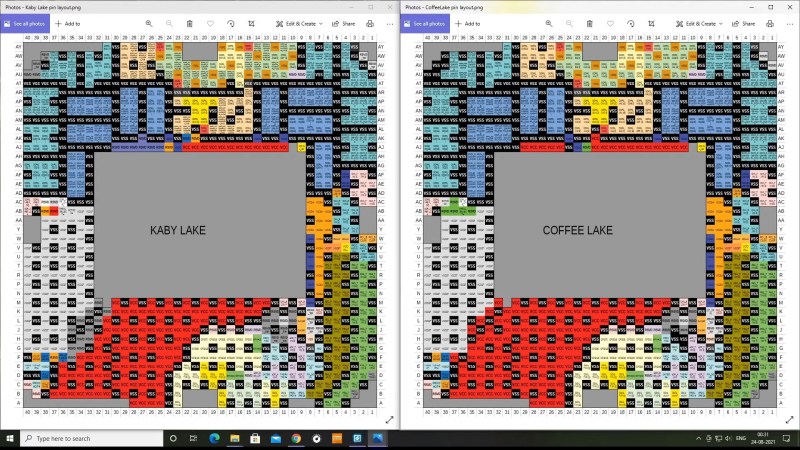
Intel’s Anti-Upgrade Tricks Defeated With Kapton Tape
If you own an Intel motherboard with a Z170 or Z270 chipset, you might believe that it only supports CPUs up to Intel’s 7th generation, known as Kaby Lake. Even the CPU socket’s pinout is different in the next generation — we are told, it will fit the same socket, but...
Mystery attacker remotely bricked 600,000 SOHO routers with malicious firmware update
Source and motive of 'Pumpkin Eclipse' attack unknown Unknown miscreants broke into more than 600,000 routers belonging to a single ISP late last year and deployed malware on the devices before totally disabling them, according to security researchers.…
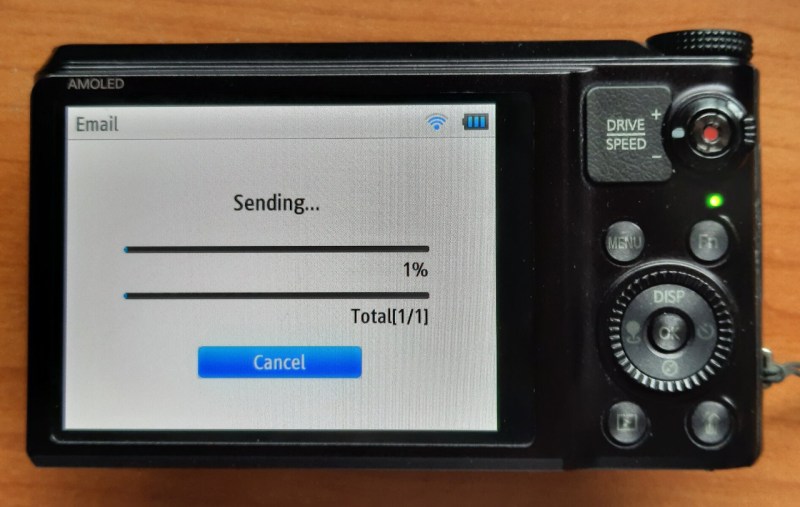
Fixing A Camera’s WiFi Connectivity With Ghidra
If your old camera’s WiFi picture upload feature breaks, what do you do? Begrudgingly get a new one? Well, if you’re like [Ge0rg], you break out Ghidra and find the culprit. He’s been hacking on Samsung’s connected cameras for a fair bit now, and we’ve covered his...
Euro cops disrupt malware droppers, seize thousands of domains
Operation Endgame just beginning: 'Stay tuned,' says Europol An international law enforcement operation led by Europol has kicked off with the announcement of multiple arrests, searches, seizures and takedowns of malware droppers and their operators.…
Largest international police operation against botnets takes down ransomware networks
Police coordinated by the European Union’s justice and police agencies have taken down computer networks responsible for spreading ransomware via infected emails, in what they called the biggest ever international operation against the lucrative form of cybercrime.The...
CISA Alerts Federal Agencies to Patch Actively Exploited Linux Kernel Flaw
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Thursday added a security flaw impacting the Linux kernel to the Known Exploited Vulnerabilities (KEV) catalog, citing evidence of active exploitation. Tracked as CVE-2024-1086 (CVSS score: 7.8), the...
FlyingYeti Exploits WinRAR Vulnerability to Deliver COOKBOX Malware in Ukraine
Cloudflare on Thursday said it took steps to disrupt a month-long phishing campaign orchestrated by a Russia-aligned threat actor called FlyingYeti targeting Ukraine. "The FlyingYeti campaign capitalized on anxiety over the potential loss of access to housing and...
Mystery malware destroys 600k routers from a single ISP during 72-hour span
Article URL: https://blog.lumen.com/the-pumpkin-eclipse/ Comments URL: https://news.ycombinator.com/item?id=40525130 Points: 68 # Comments: 12
‘Operation Endgame’ Hits Malware Delivery Platforms
Article URL: https://krebsonsecurity.com/2024/05/operation-endgame-hits-malware-delivery-platforms/ Comments URL: https://news.ycombinator.com/item?id=40524823 Points: 4 # Comments: 0
RedTail Crypto-Mining Malware Exploiting Palo Alto Networks Firewall Vulnerability
The threat actors behind the RedTail cryptocurrency mining malware have added a recently disclosed security flaw impacting Palo Alto Networks firewalls to its exploit arsenal. The addition of the PAN-OS vulnerability to its toolkit has been complemented by updates to...
What Is ShrinkLocker? New Ransomware Targets Microsoft BitLocker Encryption Feature
The malware exploits Windows BitLocker to encrypt corporate files.
TrickBot and Other Malware Droppers Disrupted by Law Enforcement
The TrickBot botnet and other malware droppers have been targeted by international law enforcement in Operation Endgame. The post TrickBot and Other Malware Droppers Disrupted by Law Enforcement appeared first on SecurityWeek.
Europol Shuts Down 100+ Servers Linked to IcedID, TrickBot, and Other Malware
Europol on Thursday said it shut down the infrastructure associated with several malware loader operations such as IcedID, SystemBC, PikaBot, SmokeLoader, Bumblebee, and TrickBot as part of a coordinated law enforcement effort codenamed Operation Endgame. "The actions...
Cybercriminals pose as “helpful” Stack Overflow users to push malware
Article URL: https://www.bleepingcomputer.com/news/security/cybercriminals-pose-as-helpful-stack-overflow-users-to-push-malware/ Comments URL: https://news.ycombinator.com/item?id=40521229 Points: 10 # Comments: 3
Operation Endgame – 16,455,383 breached accounts
In May 2024, a coalition of international law enforcement agencies took down a series of botnets in a campaign they coined "Operation Endgame". Data seized in the operation included impacted email addresses and passwords which were provided to HIBP to help victims...
Brazilian Banks Targeted by New AllaKore RAT Variant Called AllaSenha
Brazilian Banks Targeted by New AllaKore RAT Variant Called AllaSenha Go to Source Brazilian banking institutions are the target of a new campaign that distributes a custom variant of the Windows-based AllaKore remote access trojan...
North Korea building cash reserves using ransomware, video games
North Korea building cash reserves using ransomware, video games Go to Source Microsoft says Kim’s hermit nation is pivoting to latest tools as it evolves in cyberspace A brand-new cybercrime group that Microsoft ties to North Korea...
Microsoft Uncovers ‘Moonstone Sleet’ — New North Korean Hacker Group
Microsoft Uncovers 'Moonstone Sleet' — New North Korean Hacker Group Go to Source A never-before-seen North Korean threat actor codenamed Moonstone Sleet has been attributed as behind cyber attacks targeting individuals and...
Researchers Warn of CatDDoS Botnet and DNSBomb DDoS Attack Technique
The threat actors behind the CatDDoS malware botnet have exploited over 80 known security flaws in various software over the past three months to infiltrate vulnerable devices and co-opt them into a botnet for conducting distributed denial-of-service (DDoS) attacks....
Pakistan-linked Hackers Deploy Python, Golang, and Rust Malware on Indian Targets
The Pakistan-nexus Transparent Tribe actor has been linked to a new set of attacks targeting Indian government, defense, and aerospace sectors using cross-platform malware written in Python, Golang, and Rust. "This cluster of activity spanned from late 2023 to April...
5 not-so-obvious ways to speed up Windows 11
5 not-so-obvious ways to speed up Windows 11 Go to Source It seems like the more powerful computers get, the more noticeable it is once they start to buckle under the pressure of multi-tabbed web sessions, unchecked digital hoarding,...
