Microsoft Edge Bug Could Have Allowed Attackers to Silently Install Malicious Extensions
Microsoft Edge Bug Could Have Allowed Attackers to Silently Install Malicious Extensions Go to Source A now-patched security flaw in the Microsoft Edge web browser could have been abused to install arbitrary extensions on users'...

Cyber Security Today, March 27, 2024 – A botnet exploits old routers, a new malware loader discovered, and more warnings about downloading code from open source repositories
A botnet exploits old routers, a new malware loader discovered, and more warnings about downloading code from open source repositories. Welcome to Cyber Security Today. It’s Wednesday March 27th, 2024. I’m Howard Solomon, contributing reporter on cybersecurity for...
Alert: New Phishing Attack Delivers Keylogger Disguised as Bank Payment Notice
A new phishing campaign has been observed leveraging a novel loader malware to deliver an information stealer and keylogger called Agent Tesla. Trustwave SpiderLabs said it identified a phishing email bearing this attack chain on March 8, 2024. The message masquerades...
GSM Hosting – 2,607,440 breached accounts
In August 2016, breached data from the vBulletin forum for GSM-Hosting appeared for sale alongside dozens of other hacked services. The breach impacted 2.6M users of the service and included email and IP addresses, usernames and salted MD5 password hashes.
Researchers Discover 40,000-Strong EOL Router, IoT Botnet
Malware hunters sound an alarm after discovering a 40,000-strong botnet packed with end-of-life routers and IoT devices being used in cybercriminal activities. The post Researchers Discover 40,000-Strong EOL Router, IoT Botnet appeared first on SecurityWeek.
Flipping Pages: New Linux vulnerability in nf_tables and exploitation techniques
Article URL: https://pwning.tech/nftables/ Comments URL: https://news.ycombinator.com/item?id=39828424 Points: 230 # Comments: 57
SwordFantasy – 2,690,657 breached accounts
In January 2019, the now defunct MMO and RPG game SwordFantasy suffered a data breach that exposed 2.7M unique email addresses. Other impacted data included username, IP address and salted MD5 password hashes.
Show HN: Tracecat – Open-source security alert automation / SOAR alternative
Hi HN, we are building Tracecat (https://tracecat.com/), an open source automation platform for security alerts. Tracecat automates the tasks a security analyst has to do when responding to a security alert: e.g. contact victims, investigate security logs, report...
GoFetch security exploit can’t be disabled on M1 and M2 Apple chips
For now, cryptographic work should be run on slower Icestorm cores The GoFetch vulnerability found on Apple M-series and Intel Raptor Lake CPUs has been further unpacked by the researchers who first disclosed it.…
Top Python Developers Hacked in Sophisticated Supply Chain Attack
Multiple Python developers get infected after downloading malware-packed clone of the popular tool Colorama. The post Top Python Developers Hacked in Sophisticated Supply Chain Attack appeared first on SecurityWeek.
Key Lesson from Microsoft’s Password Spray Hack: Secure Every Account
Key Lesson from Microsoft’s Password Spray Hack: Secure Every Account Go to Source In January 2024, Microsoft discovered they’d been the victim of a hack orchestrated by Russian-state hackers Midnight Blizzard (sometimes known as...
Microsoft confirms memory leak in March Windows Server security update
ALSO: Viasat hack wiper malware is back, users are the number one cause of data loss, and critical vulns Infosec in brief If your Windows domain controllers have been crashing since a security update was installed earlier this month, there's no longer any need to...
The new Windows update made me think I’d installed malware
Article URL: https://www.pcgamer.com/software/windows/the-new-windows-update-made-me-think-id-installed-malware-but-it-was-just-microsofts-latest-attempt-to-try-and-fool-me-into-using-bing/ Comments URL: https://news.ycombinator.com/item?id=39809478 Points: 11 #...
Shrouded Horizons: My Passage to the Dark Web Marketplaces
The dark web is open to anyone with a Tor browser and a flashlight. Cybersecurity expert finds a marketplace called AlphaBay with more than 30,000 listings. There are also listings for malware and stolen data, like Social Security numbers and credit card details. The...
N. Korea-linked Kimsuky Shifts to Compiled HTML Help Files in Ongoing Cyberattacks
The North Korea-linked threat actor known as Kimsuky (aka Black Banshee, Emerald Sleet, or Springtail) has been observed shifting its tactics, leveraging Compiled HTML Help (CHM) files as vectors to deliver malware for harvesting sensitive data. Kimsuky, active since...
Investors’ pledge to fight spyware undercut by past investments in US malware maker
On Monday, the Biden administration announced that six new countries had joined an international coalition to fight the proliferation of commercial spyware, sold by companies such as NSO Group or Intellexa. Now, some investors have announced that they too are...
Apple Chip Flaw Leaks Secret Encryption Keys
Plus: The Biden administration warns of nationwide attacks on US water systems, a new Russian wiper malware emerges, and China-linked hackers wage a global attack spree.
Russian Hackers Use ‘WINELOADER’ Malware to Target German Political Parties
The WINELOADER backdoor used in recent cyber attacks targeting diplomatic entities with wine-tasting phishing lures has been attributed as the handiwork of a hacking group with links to Russia's Foreign Intelligence Service (SVR), which was responsible for breaching...
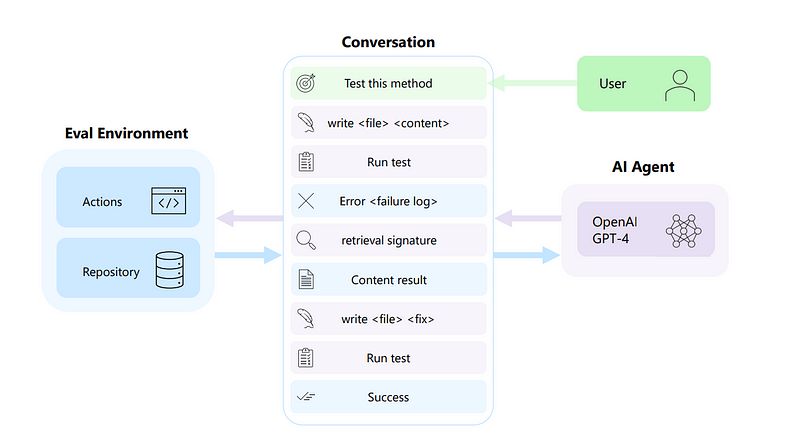
From Davin to Microsoft Autodev: Elevating AI Coding Assistants to Super-Powered Code Editors
From Davin to Microsoft Autodev: Elevating AI Coding Assistants to Super-Powered Code Editors Go to Source Tools like ChatGPT have been a big help for programmers, offering code suggestions in chat and even directly within their...
39,000 Websites Infected in ‘Sign1’ Malware Campaign
Over 39,000 websites have been infected with the Sign1 malware that redirects visitors to scam domains. The post 39,000 Websites Infected in ‘Sign1’ Malware Campaign appeared first on SecurityWeek.
China-Linked Group Breaches Networks via Connectwise, F5 Software Flaws
A China-linked threat cluster leveraged security flaws in Connectwise ScreenConnect and F5 BIG-IP software to deliver custom malware capable of delivering additional backdoors on compromised Linux hosts as part of an "aggressive" campaign. Google-owned Mandiant...
Implementing Zero Trust Controls for Compliance
The ThreatLocker® Zero Trust Endpoint Protection Platform implements a strict deny-by-default, allow-by-exception security posture to give organizations the ability to set policy-based controls within their environment and mitigate countless cyber threats, including...
MediaWorks – 162,710 breached accounts
In March 2024, millions of rows of data from the New Zealand media company MediaWorks was publicly posted to a popular hacking forum. The incident exposed 163k unique email addresses provided by visitors who filled out online competitions and included names, physical...
Russian Hackers Target Ukrainian Telecoms with Upgraded ‘AcidPour’ Malware
The data wiping malware called AcidPour may have been deployed in attacks targeting four telecom providers in Ukraine, new findings from SentinelOne show. The cybersecurity firm also confirmed connections between the malware and AcidRain, tying it to threat activity...
Why x86 Needs To Die
As I’m sure many of you know, x86 architecture has been around for quite some time. It has its roots in Intel’s early 8086 processor, the first in the family. Indeed, even the original 8086 inherits a small amount of architectural structure from Intel’s 8-bit...
Microsoft Patches Xbox Vulnerability Following Public Disclosure
Microsoft Patches Xbox Vulnerability Following Public Disclosure Go to Source Microsoft patches Xbox Gaming Services vulnerability CVE-2024-28916 after initially saying it was not a security issue. The post Microsoft Patches Xbox...
AndroxGh0st Malware Targets Laravel Apps to Steal Cloud Credentials
Cybersecurity researchers have shed light on a tool referred to as AndroxGh0st that's used to target Laravel applications and steal sensitive data. "It works by scanning and taking out important information from .env files, revealing login details linked to AWS and...
Launch HN: CamelQA (YC W24) – AI that tests mobile apps
Hey HN! We're camelQA (https://camelqa.com/). We’re building an AI agent that can automate mobile devices using computer vision. Our first use case is for mobile app QA. We convert natural language test cases into tests that run on real iOS and Android devices in our...
Android malware, Android malware and more Android malware
Article URL: https://securelist.com/crimeware-report-android-malware/112121/ Comments URL: https://news.ycombinator.com/item?id=39765003 Points: 11 # Comments: 0
New BunnyLoader Malware Variant Surfaces with Modular Attack Features
Cybersecurity researchers have discovered an updated variant of a stealer and malware loader called BunnyLoader that modularizes its various functions as well as allow it to evade detection. "BunnyLoader is dynamically developing malware with the capability to steal...
